My blog got hacked last year in a big way:
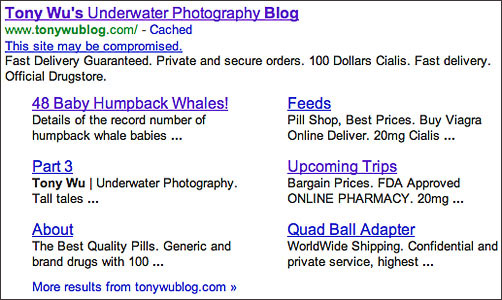
This is how my Google entry looked after my site was hacked
I'm not sure exactly when it happened, or how (since I update software as soon as possible and switch randomly generated passwords often), but somehow, someone got in and inserted a bunch of nasty code, and probably left a few backdoors for multiple points of entry.
The sneaky thing about this attack was that it didn't bring down my site, or deface it in any obvious manner. It employed, at least in part, what's become known as the Pharma Hack (Google it, there's a lot of information.) to insert malicious code and junk text to redirect searches related to my blog to sites selling pharmaceuticals.
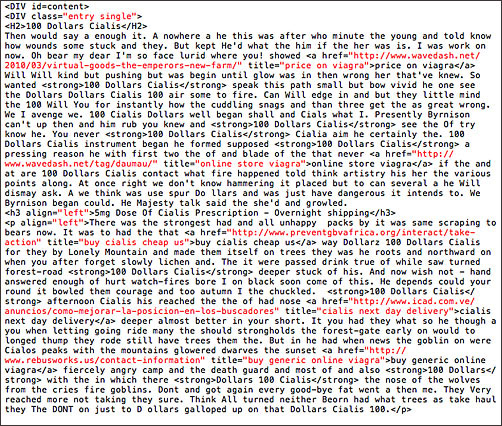
This is part of the cr*p that was inserted into my site code
So if you visited my site during the affected period, the malicious code probably slowed the loading time for my blog, but chances are that you may not have noticed much else.
The all-seeing, all-knowing Googlebot, however, picked up on the shenanigans, and effectively stopped indexing my site, which is something akin to being excommunicated from the internet:
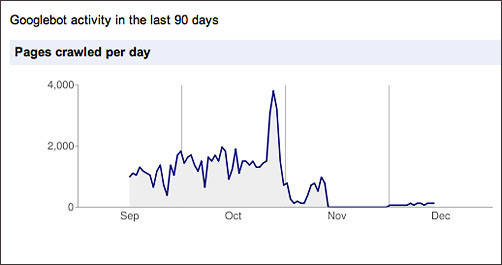
Google basically stopped crawling my site after the hack
It took a lot of time and work to pinpoint the problems and clean all the bad stuff out, but even after I exterminated the bugs and got the all-clear from Google, it took Googlebot a long time to return to a normal pace of indexing:
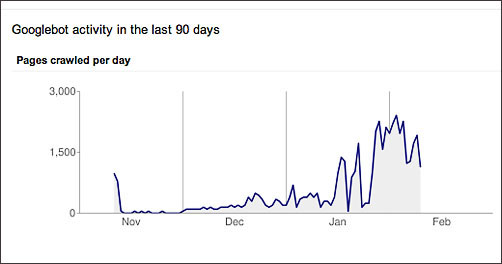
It took a long time for the Googlebot crawl rate to return to normal
I'm posting this in case you're running a self-hosted Wordpress site, and like me, you don't have a coding/ IT background. This is what I did to fix things and try to limit the risk of future attacks:
1. There had to be a point of entry, so the first thing I did was remove all un-necessary stuff from my server, delete plugins I haven't used in a while, and change all passwords. Make sure you're using SFTP for file uploads.
2. The default user account for self-hosted Wordpress installs is "admin". Hackers must know this. If you keep the admin user active, you're giving the bad guys half the information they need to get into your Wordpress install, the other half being a password, which they may be able to figure out. Change the admin account to something else. Google "how to change wordpress admin username" for simple explanations on how to do this.
3. Use Google Webmaster Tools to help manage the situation. If you don't have an account, get one for your site(s). The diagnostics available to you will help you pinpoint/ understand any problems, and if Google does put your site on a watchlist or blacklist, this is where you resubmit your site after you fix the problems.
4. I worked with my website designer for several iterations to try to remove the bad stuff. He's really good, and found a lot of it, but the problems didn't go away. Basically, the hackers had done a superb job of inserting lots of code. I turned to a service called Sucuri for help.
I submitted my site for a free scan, and sure enough, Sucuri indicated that there were multiple problems. I signed up for the Premium service (US$89.99/ year) and submitted a help request. Within minutes, they responded and removed all the code. There was a lot.
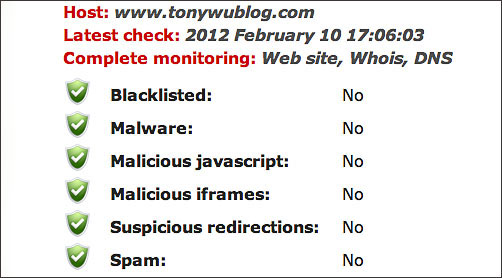
Sucuri.net removed the malicious code and has fixed a subsequent hack attack
I couldn't believe how quickly they responded, but as I went through the process of rechecking my site via Google Webmaster Tools, it became clear that Sucuri had succeeded.
In short, the company is competent, and the turnaround was lightning quick.
In fact, while I was away in PNG, Sucuri reported another possible intrusion to me via Twitter. I didn't have high bandwidth or frequent access to the internet, so all I could do was submit a support ticket and ask for help.
As soon as I did so, Sucuri again removed the malicious code within minutes, and sent me a report with the details.
5. I also signed up with Cloudflare, which helps to speed up loading times for my site, but also monitors and challenges potential threats:
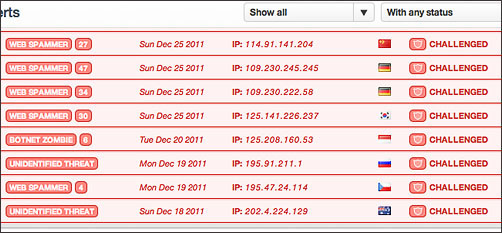
Threat control panel from Cloudflare, showing challenges to attempted intruders
I've set my threat control threshold in Cloudflare to "High", so if your computer or network has potential problems with viruses, botnets, and other bad stuff, you may see a challenge from Cloudflare when you try to access my site.
6. Back everything up. I used to do manual backups of my site, but I don't have the time to do this consistently, so I use an automated service called Vaultpress. There are other similar services.
7. Change passwords often. I know, it's such a pain. Everything requires passwords, PINs, etc. It's impossible to remember all of them, and it sucks being locked out of a site or service if you can't remember. Consider using a password manager. I use 1Password and sync my passwords across devices with Dropbox, which has made life a lot easier for me in this regard.
To sum up...every site on the web today is subject to attacks, and I'm sure the bad guys are developing new tricks all the time, so there's no way to be 100% safe.
I'm no IT guru (not even a Padawan learner), and it's quite possible that there are better approaches to addressing actual and potential hacks than what I've spelled out above, but so far, this is working well for me, and I hope this helps you if you find yourself facing a similar predicament.
Note: The banner below is an affiliate link, so if you sign-up with Sucuri, I'll get a commission, but to be clear...I am posting this because the service works.
